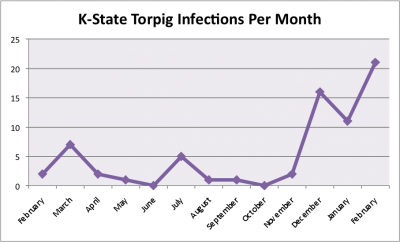
Silently sneaking onto your computer, Torpig lies in wait for you to log in to your bank’s website and sends your account information to well-organized criminals. Torpig has found its way on to more than 70 computers at K-State in the last year, and the number of infections is on the rise. The chart below shows infections from February 2009 through February 2010.
Unfortunately, security technology can’t always prevent infection because the malicious software changes rapidly and uses sophisticated stealth techniques to hide itself on infected computers. Thus, once again the user plays a key role in preventing infection and financial fraud.
Torpig, also known as Sinowal or Anserin, is malicious software belonging to the Trojan horse family that is designed to steal sensitive information from the computer that it infects. It specifically targets personal and corporate financial information such as credit card data, usernames, and passwords used in the victim’s web browser. It’s constantly changing and evolving and employs rootkit functionality to make it very difficult to detect and remove.
Torpig initially infects computers in several different ways. It takes advantage of a number of vulnerabilities in older versions of web browsers and other popular software such as Adobe Reader, Flash, and Java. The attackers must simply get the vulnerable user to visit an infected website and the browser will download the Trojan without any user interaction. Attackers may use phishing e-mails to get users to visit an infected website. They’ve also started buying advertisements from popular legitimate websites that redirect users to infected servers, a practice known as malvertising.
Originally developed in 2005, Torpig has managed to evade detection by most antivirus and malware detection utilities. Torpig is most commonly distributed along with another rootkit known as Mebroot, which infects the Master Boot Record of the victim machine. The MBR controls the loading of the operating system stored on the hard drive, so that means that Mebroot gets loaded before the OS does, and then hides its existence from the OS.
Once a computer is infected, it joins a network of other infected computers known as a botnet and checks in with a command and control server to get instructions. Monitoring this network communication is the most common way we detect Torpig infections, but due to the ever-changing nature of its communication methods and the volume of normal traffic that it hides in, detection is somewhat unreliable. Torpig also hides its files from the users using its rootkit functionality and encrypts its log files, making it quite difficult for antivirus software or even a skilled user to detect.
Modern malware doesn’t necessarily require the user to make a bad decision to get infected, so to reduce your risk of being infected with Torpig as well as other malware, follow these protective measures:
- Keep all of your Windows patches up-to-date.
- Keep your web browsers, such as Internet Explorer and Firefox, up-to-date with the latest security patches.
- Update all of your Adobe products, such as Adobe Flash and Adobe Reader.
- If you have Java installed, make sure its security patches are up-to-date.
- Make sure you’re running current antivirus software. TrendMicro OfficeScan can detect some variants of Torpig, but like all other antivirus software, it can’t immediately identify new versions of this constantly-changing malware.
- Run the Secunia Online Software Inspector to check current vulnerabilities.
And, as always, don’t click on links or open attachments in unexpected e-mails. If you suspect that you may have been infected with the Torpig Trojan, contact your IT support person and K-State’s security team. We may be able to determine what information was stolen by criminals and which passwords you need to change.