 At K-State, the security of our devices and data remains a top priority. As technology evolves, so do the measures we take to ensure the safety of our digital environment.
At K-State, the security of our devices and data remains a top priority. As technology evolves, so do the measures we take to ensure the safety of our digital environment.
For University-owned devices, we are pleased to inform you that K-State provides Microsoft Defender as the primary antivirus solution. Microsoft Defender is a comprehensive security solution that offers real-time protection against a wide range of threats, ensuring that our university devices remain secure and up to date. Windows machines joined to K-State’s network should already have this software installed. If you are using a macOS device, you may need to install the software manually if your department is not deploying it via a device management tool. If you are unsure whether Defender is installed, look for this icon in your menu bar. Continue reading “Important update on antivirus software for K-State devices”
 Visit The Division of IT training page to see various training opportunities. The following is a glimpse of what you can find there:
Visit The Division of IT training page to see various training opportunities. The following is a glimpse of what you can find there: Qualtrics is a powerful survey platform with many features. One of those features is Workflows. Workflows allow you to automate tasks such as sending a survey completion email to participants.
Qualtrics is a powerful survey platform with many features. One of those features is Workflows. Workflows allow you to automate tasks such as sending a survey completion email to participants.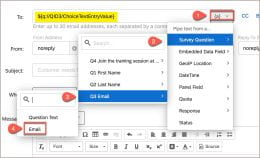 In the To box, click the down arrow.
In the To box, click the down arrow. Microsoft Teams offers a diverse array of features designed to supercharge your productivity and foster seamless collaboration
Microsoft Teams offers a diverse array of features designed to supercharge your productivity and foster seamless collaboration







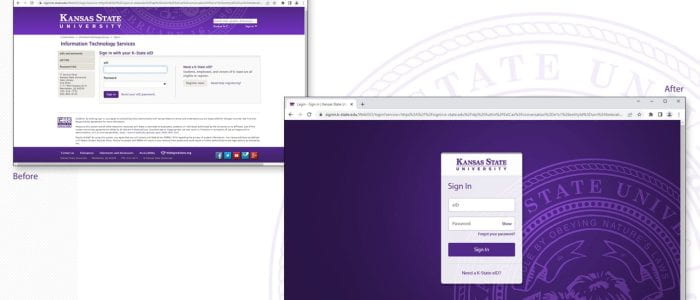
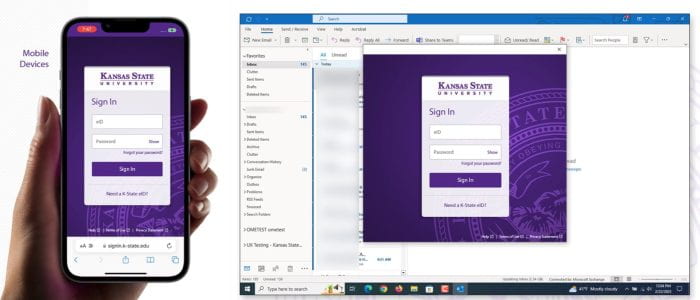
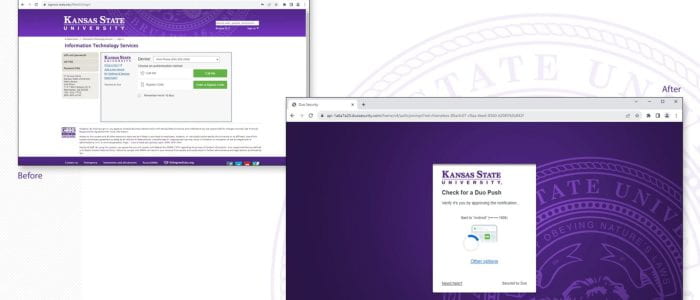
 Explore the free resources and services offered by the Division of Information Technology to kickstart your semester!
Explore the free resources and services offered by the Division of Information Technology to kickstart your semester! The Internet touches almost all aspects of our daily lives. We can shop, bank, connect with family and friends, and handle our medical records all online. These activities require you to provide personally identifiable information (PII) such as your name, date of birth, account numbers, passwords, and location information. Be diligent when sharing personal information online to reduce the risk of becoming a victim of a cybercrime.
The Internet touches almost all aspects of our daily lives. We can shop, bank, connect with family and friends, and handle our medical records all online. These activities require you to provide personally identifiable information (PII) such as your name, date of birth, account numbers, passwords, and location information. Be diligent when sharing personal information online to reduce the risk of becoming a victim of a cybercrime.