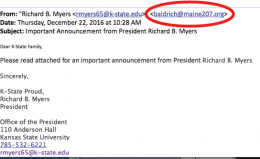
Imagine my surprise to open an email and learn that I was about to send pornography and video footage to ten randomly selected individuals from my contact list, should I not comply with the demands of $2,000 in bitcoins within 24 hours. Where my heart skipped a beat was in the subject line that included an old password and the first sentence of the email that included the same password.
Here’s how the email started:
“𝙸𝚝 𝚜𝚎𝚎𝚖𝚜 𝚝𝚑𝚊𝚝, ——–, 𝚒𝚜 𝚢𝚘𝚞𝚛 𝚙𝚊𝚜𝚜𝚠𝚘𝚛𝚍.”
According to our security experts, this password could have been harvested years ago, stored on the dark web and then sold to scammers –some nefarious individual(s) with too much time on their hands.
After more deep breathing and internet searches, I found this to be an old scam but with a new scarier twist, the revealing of a password. It also listed how many days the scammer had been capturing information about me – 182 days.
What did I do? After a few more deep breaths, I did the following:
- Sent the email with headers to abuse@ksu.edu.
- Discussed the email with our technical support staff
- Checked the scams blog to determine if this had been reported
- Changed my password on every system where I had used the old password.
- Ran malware software on my computer
- Deleted the email
- Remain vigilant about scams
A couple of red flags I noted from the email were the urgency and intimidation of the request (𝚛𝚎𝚚𝚞𝚒𝚛𝚎 𝚢𝚘𝚞𝚛 𝚏𝚞𝚕𝚕 𝚊𝚝𝚝𝚎𝚗𝚝𝚒𝚘𝚗 𝚏𝚘𝚛 𝚝𝚑𝚎 𝚞𝚙 𝚌𝚘𝚖𝚒𝚗𝚐 𝚃𝚠𝚎𝚗𝚝𝚢-𝚏𝚘𝚞𝚛 𝚑𝚘𝚞𝚛𝚜), the demand for money (𝙿𝚞𝚛𝚌𝚑𝚊𝚜𝚎 $ 𝟸𝟶𝟶𝟶 𝚒𝚗 𝚋𝚒𝚝𝚌𝚘𝚒𝚗 𝚊𝚗𝚍 𝚜𝚎𝚗𝚍 𝚝𝚑𝚎𝚖 𝚘𝚗 𝚝𝚑𝚎 𝚋𝚎𝚕𝚘𝚠 𝚊𝚍𝚍𝚛𝚎𝚜𝚜), the email from an individual I didn’t know (mpnaneteps@hotmail.com), poorly worded email and incorrect use of capitalization.
The university has been busy processing these scams over the last week. If you are unsure about an email send to abuse and then delete. My mantra continues, when in doubt don’t give it out (your credentials).
 Cybersecurity Awareness Training is required by state statute for all K-State employees every year.
Cybersecurity Awareness Training is required by state statute for all K-State employees every year.
 Users of Mac computers are asked to download the latest security update from Zoom when prompted to do so. The vulnerability found earlier this summer would allow hackers to launch a Zoom meeting without prior knowledge. Zoom released a patch on July 9 and is asking users to install the patch.
Users of Mac computers are asked to download the latest security update from Zoom when prompted to do so. The vulnerability found earlier this summer would allow hackers to launch a Zoom meeting without prior knowledge. Zoom released a patch on July 9 and is asking users to install the patch.