Imagine your digital world as a fortress, with each software update serving as an essential reinforcement to its walls. When you see that familiar “Update Available” notification, do you click “Remind me later” and carry on with your online activities, inadvertently leaving a crack in your fortress’s defenses? In an era of ever-evolving cyber threats, this article reminds us why staying vigilant against unpatched vulnerabilities is our frontline defense. Today, we explore the critical realm of software updates and their importance in fortifying your digital stronghold against relentless adversaries. Continue reading “Cybersecurity Awareness: Think twice before you skip that update!”
Imagine your digital world as a fortress, with each software update serving as an essential reinforcement to its walls. When you see that familiar “Update Available” notification, do you click “Remind me later” and carry on with your online activities, inadvertently leaving a crack in your fortress’s defenses? In an era of ever-evolving cyber threats, this article reminds us why staying vigilant against unpatched vulnerabilities is our frontline defense. Today, we explore the critical realm of software updates and their importance in fortifying your digital stronghold against relentless adversaries. Continue reading “Cybersecurity Awareness: Think twice before you skip that update!”
Category: Cybersecurity
Cybersecurity Awareness: Password safety tips for all of your accounts
 In the digital age, your passwords are your first line of defense against online threats. Yet, many of us still rely on weak and easily guessable passwords. It’s like locking your front door but leaving the key under the mat. In this article, we’ll provide you with practical tips to strengthen your password security without overwhelming you. Let’s get started on the path to safeguarding your online accounts.
In the digital age, your passwords are your first line of defense against online threats. Yet, many of us still rely on weak and easily guessable passwords. It’s like locking your front door but leaving the key under the mat. In this article, we’ll provide you with practical tips to strengthen your password security without overwhelming you. Let’s get started on the path to safeguarding your online accounts.
The good news is that creating and storing strong passwords with the help of a password manager is one of the easiest ways to protect ourselves from someone logging into our accounts and stealing sensitive information, data, money, or even our identities. Continue reading “Cybersecurity Awareness: Password safety tips for all of your accounts”
Important update on antivirus software for K-State devices
 At K-State, the security of our devices and data remains a top priority. As technology evolves, so do the measures we take to ensure the safety of our digital environment.
At K-State, the security of our devices and data remains a top priority. As technology evolves, so do the measures we take to ensure the safety of our digital environment.
For University-owned devices, we are pleased to inform you that K-State provides Microsoft Defender as the primary antivirus solution. Microsoft Defender is a comprehensive security solution that offers real-time protection against a wide range of threats, ensuring that our university devices remain secure and up to date. Windows machines joined to K-State’s network should already have this software installed. If you are using a macOS device, you may need to install the software manually if your department is not deploying it via a device management tool. If you are unsure whether Defender is installed, look for this icon in your menu bar. Continue reading “Important update on antivirus software for K-State devices”
Don’t take the bait: Tips to avoid social engineering attacks
In today’s interconnected world, where technology plays an ever-expanding role in our lives, safeguarding your digital presence is of primary importance. Social engineering attacks have emerged as a pervasive threat, relying on the manipulation of human psychology to gain unauthorized access to sensitive information.

Continue reading “Don’t take the bait: Tips to avoid social engineering attacks”
K-State is now using geolocation

Over the summer, K-State began using geolocation to assist in safeguarding accounts from being compromised by utilizing IP information on computers and mobile devices. With geolocation, users will be alerted of suspicious attempts to access K-State accounts. If suspicious activity is recognized, the user will receive an email notification of the activity with recommendations on the next steps, which could include updating account passwords.
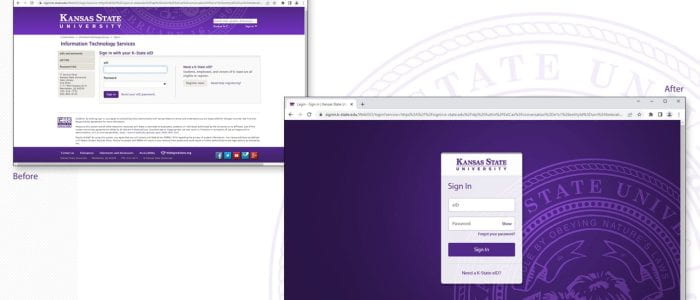
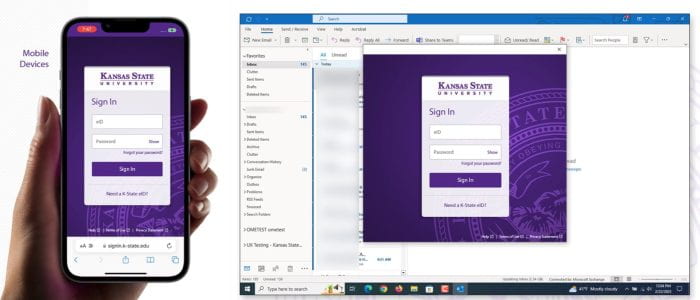
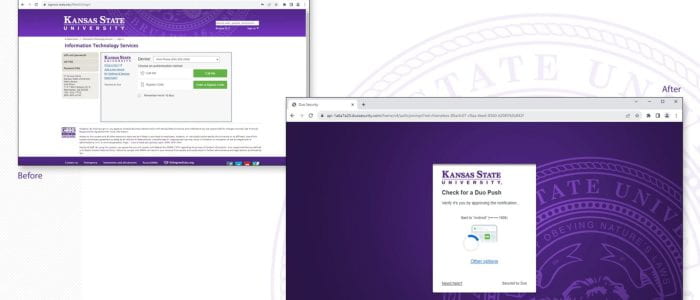
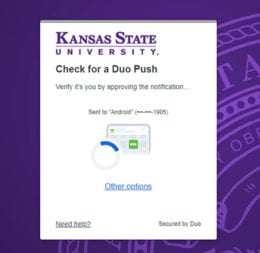
Sept. 19: A new look for Single Sign-On (SSO) and Duo Two-Factor Authentication
On Sept. 19, a day after the fall semester Census day, The Division of Information Technology (IT) will release a sleeker version of Single Sign-On (SSO) and the newest iteration of Duo’s two-factor authentication, known as Duo Universal Prompt. You can expect a refreshed look and feel for both applications.
Duo Universal Prompt
The update to Duo Universal Prompt is required to safeguard your information further while providing a simplified, streamlined user experience.
The first time you use Duo Universal Prompt, Duo will choose the most secure method from those you have set up. You can use that method, or choose a different method through the new prompt’s Other Options link. After that first authentication with the new prompt, Duo will by default use the method you used most recently.
Reduce the Number of Times You Need to Authenticate Continue reading “Sept. 19: A new look for Single Sign-On (SSO) and Duo Two-Factor Authentication”
Welcome to Fall 2023!
 Explore the free resources and services offered by the Division of Information Technology to kickstart your semester!
Explore the free resources and services offered by the Division of Information Technology to kickstart your semester!
- Get a free copy of Microsoft Office for personal use on up to 5 PCs or Macs, 5 tablets, and 5 phones. See the installation instructions for Mac, Windows, and mobile devices.
- Use Microsoft 365 – an office collaboration suite that includes tools such as email, calendar, office applications, file storage space, and more. You can access the suite from your desktop, web browser, or phone.
- Connect your mobile devices to K-State’s wireless network.
- Get antivirus – K-Staters connecting their computers to the Kansas State University network can use the approved antivirus software of their choice or choose from the list of recommended software.
- Use the Qualtrics survey system. Faculty/staff and authorized students can use the Qualtrics Survey System. Qualtrics is a comprehensive survey tool with more than 90 question types, simplified reporting tools, online training modules, a library of surveys to peruse, and more.
- Use Zoom (video and audio conferencing) to meet virtually.
Use Zoom to set up an online staff meeting, a training session, a class group meeting, beam in a speaker, and more. See the Using Zoom guide to get started. - Remote access to software – Remote access to software in the K-State computer labs allows students to use specialized software and avoid having to purchase themselves. Popular software includes SAS, SPSS, Mathematica, and Matlab. Unfortunately, Adobe Creative Cloud is not available for remote access. To see a list of all software available in the computing labs, visit the Software in the Computing Labs page. To learn how to access the software, visit the Remote Access page.
- Get IT Help
More IT resources for K-Staters are on the Welcome to IT at K-State website.
CatFiles W: Drive to be reorganized
Phase One of the CatFiles reorganization project (Y: Drive) was completed in 2022, and Phase Two (W: Drive) is now underway. CatFiles was the central file server at K-State for many years. Storage technology has improved over the years, and security threats have increased. For those reasons, the strategic decision has been made to reorganize CatFiles.

Archives and Records Management has partnered with the Division of Information Technology for this project. K-State Libraries is currently taking part in a pilot to help determine the best policies and procedures for this enormous undertaking that will affect 160 departments. More information will be provided about the timeline, archiving process, and storage options in the coming months.
While the long-term goal is to reduce the usage of W: Drive, all the current CatFiles W: Drive business needs must first be addressed. We appreciate your patience as we create an organization process while following the K-State’s Records Retention Policies. Continue reading “CatFiles W: Drive to be reorganized”
Protect your online privacy
 The Internet touches almost all aspects of our daily lives. We can shop, bank, connect with family and friends, and handle our medical records all online. These activities require you to provide personally identifiable information (PII) such as your name, date of birth, account numbers, passwords, and location information. Be diligent when sharing personal information online to reduce the risk of becoming a victim of a cybercrime.
The Internet touches almost all aspects of our daily lives. We can shop, bank, connect with family and friends, and handle our medical records all online. These activities require you to provide personally identifiable information (PII) such as your name, date of birth, account numbers, passwords, and location information. Be diligent when sharing personal information online to reduce the risk of becoming a victim of a cybercrime.
Tips to stay safe online
- Double your login protection. Enable multi-factor authentication (MFA) to ensure that the only person who has access to your account is you. Use it for email, banking, social media, and any other service that requires logging in. If MFA is an option, enable it by using a trusted mobile device, such as your smartphone, an authenticator app, or a secure token—a small physical device that can hook onto your key ring.
- Shake up your password protocol. Use the longest password or passphrase permissible. Get creative and customize your standard password for different sites, which can prevent cybercriminals from gaining access to these accounts and protect you in the event of a breach. Use password managers to generate and remember different, complex passwords for each account.
- Keep up to date. Keep your software updated to the latest version available. Maintain your security settings to keep your information safe by turning on automatic updates so you don’t have to think about it, and set your security software to run regular scans.
- Play hard to get with strangers. Cybercriminals use phishing tactics, hoping to trick their victims. If you’re unsure who an email is from—even if the details appear accurate— or if the email looks “phishy,” do not respond, and do not click on any links or attachments found in that email. When available, use the “junk” or “block” option to no longer receive messages from a particular sender.
- Never click and tell. Limit what information you post on social media—from personal addresses to where you like to grab a coffee. Many people don’t realize that these seemingly random details are all criminals need to know to target you, your loved ones, and your physical belongings—online and in the real world. Keep Social Security numbers, account numbers, and passwords private, as well as specific information about yourself, such as your full name, address, birthday, and even vacation plans. Disable location services that allow anyone to see where you are—and where you aren’t—at any given time.
- Keep tabs on your apps. Most connected appliances, toys, and devices are supported by a mobile application. Your mobile device could be filled with suspicious apps running in the background or using default permissions you never realized you approved—gathering your personal information without your knowledge while also putting your identity and privacy at risk. Check your app permissions and use the “rule of least privilege” to delete what you don’t need or no longer use. Learn to just say “no” to privilege requests that don’t make sense. Only download apps from trusted vendors and sources.
- Stay protected while connected. Before you connect to any public wireless hotspot—such as at an airport, hotel, or café—be sure to confirm the name of the network and exact login procedures with the appropriate staff to ensure that the network is legitimate. If you use an unsecured public access point, practice good Internet hygiene by avoiding sensitive activities (e.g., banking) requiring passwords or credit cards. Your personal hotspot is often a safer alternative to free Wi-Fi. Only use sites that begin with “https://” when online shopping or banking.
If you receive a questionable email and prefer to play it safe, you can send it to abuse@ksu.edu. K-State’s IT Security Team will investigate the email and inform you if it is legitimate.
When to use K-State’s VPN
 Are you traveling for work this summer? Remember to use GlobalProtect, K-State’s Virtual Private Network (VPN). When working offsite, the VPN should be used when you need to access protected proprietary and confidential data and campus resources. From off-campus, use the VPN to connect to campus resources securely.
Are you traveling for work this summer? Remember to use GlobalProtect, K-State’s Virtual Private Network (VPN). When working offsite, the VPN should be used when you need to access protected proprietary and confidential data and campus resources. From off-campus, use the VPN to connect to campus resources securely.
To use the VPN software, you must be a K-State student or employee with an active K-State eID and internet connection.