Hackers have been VERY successful at tricking K-Staters into giving away their eID password — in 2009 more than 430 K-Staters replied to phishing e-mails, sending their eID passwords to criminals who used those to log into K-State’s e-mail and send thousands of spam e-mails. The good news is that repeated communications by K-State’s IT security team, Help Desk, and IT support staff have slowed the pace of compromised e-mail accounts. The bad news is the hackers’ techniques have evolved accordingly with new, more sophisticated scams that steal your password.
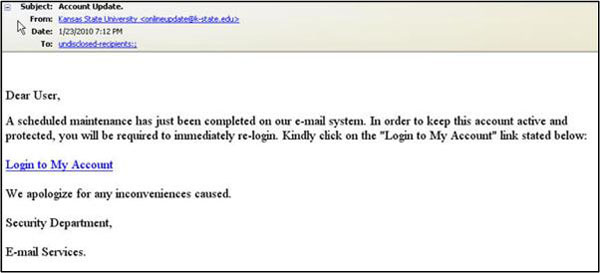
K-State’s mantra for the last two years has been “NEVER provide your password in an e-mail to anyone under any circumstances!” How did the hackers respond? On Jan. 23, they sent the following scam e-mail to numerous K-Staters. Note that it doesn’t ask you to send your password in an e-mail. Instead, it tries to trick you into clicking on a link that goes to a website where they want you to enter your eID and password.
Scam e-mail masquerading as K-State e-mail
Here’s where it gets dangerous — if you click on the link, you end up on a website hosted on a server in the Netherlands that is an exact replica of K-State’s single sign-on (SSO) page:
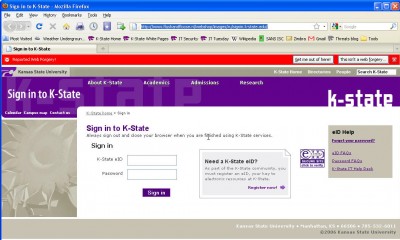
When you enter your eID and password on this fake page, they’re sent to the criminals the same as if you provided them in an e-mail. Then your browser is immediately re-directed to K-State’s homepage to make you think you successfully logged in.
Fortunately, 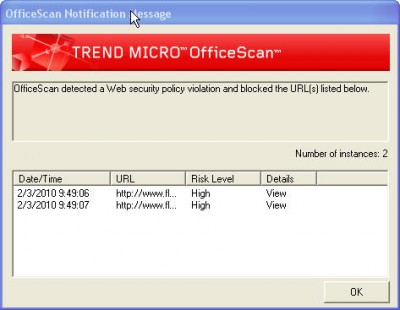 within a short time of receiving this scam e-mail, Trend Micro OfficeScan’s Web Reputation Services blocked access to this malicious replica, as did Firefox’s anti-phishing filter, thus limiting the damage done by this particular scam.
within a short time of receiving this scam e-mail, Trend Micro OfficeScan’s Web Reputation Services blocked access to this malicious replica, as did Firefox’s anti-phishing filter, thus limiting the damage done by this particular scam.
However, we can’t always rely on security technology to protect us. A similar scam e-mail received by K-Staters Jan. 28 included a website pointing to another replica of K-State’s SSO page, this time hosted in Switzerland, and neither Web Reputation Services nor Firefox blocked it right away. K-State’s IT security team had to report the malicious link to Trend Micro and Mozilla (Firefox developers) to get it blocked.
If you were tricked by either of these scams or others like it, go to K-State’s e-Profile page and change your eID password immediately.
This underscores once again that you, the user, play a critical role in protecting K-State’s information and technology resources. Please learn to recognize scams and think before you click.
This also complicates K-State’s prevention message — we can no longer simply say “don’t give away your password in an e-mail and you’ll be protected.” Everyone needs to be on the lookout for new types of scams.
Clues indicating the first e-mail was a scam
- The link in the message is hosted in the Netherlands (www.flushandfloose.nl), not K-State (www.k-state.edu).
- The body of the message does not mention K-State in any form.
- It came from “onlineupdate@k-state.edu”, which is not a valid K-State e-mail address. Don’t be fooled by the fact that the “From:” address says “Kansas State University”. That is easily forged.
- K-State’s Status of IT Resources page mentioned nothing about “scheduled maintenance” on K-State’s “e-mail system” around the time this e-mail hit campus.
- Maintenance of e-mail systems normally does not require users to “immediately re-login” in order to keep their “account active and protected.”
- It did not identify a specific individual or unit at K-State to contact if you have any questions.
- There is no unit or department called “E-mail Services” or the “Security Department” in K-State’s central Information Technology Services.