Cybercriminals know the best strategies for gaining access to your sensitive data. According to IBM’s 2014 Cyber Security Intelligence Index, human error is a factor in 95 percent of security incidents.
A few K-State stats:
- In January 2016, there were 60 phishing scams reported resulting in 9 compromised accounts. A compromised account means hackers were successful in getting a K-Stater to give up their eID and password.
- In January 2017, there were 355 phishing scams reported resulting in 313 compromised accounts!
What does this tell us?
You are the first line of defense in protecting your personal identity information. The numbers of phishing scams are going to continue to increase and the best defense is you!
Learn how to identify phishing scams and don’t give your credentials up to these criminals.
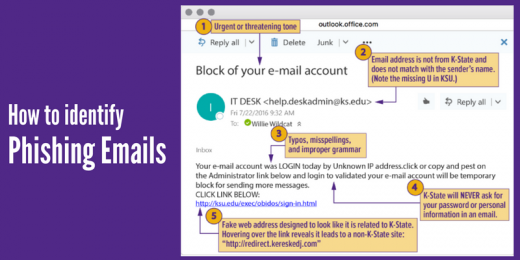
The following are a few ways to identify phishing emails:
- Know the signs. Does the e-mail contain a vague salutation, spelling or grammatical errors, an urgent request, and/or an offer that seems impossibly good? Click that delete button.
- Verify the sender. Check the sender’s e-mail address to make sure it’s legitimate. For example, if it appears that the IT Help Desk is asking you to click on a link to increase your mailbox quota, but the sender is “UniversityHelpDesk@yahoo.com,” it’s a phishing message. The K-State IT Help Desk email address is helpdesk@k-state.edu. Always mouse over a link to see where the actual link is going to take you.
- Don’t be duped by aesthetics. Phishing e-mails often contain convincing logos, links to actual company websites, legitimate phone numbers, and e-mail signatures of actual employees. However, if the message is urging you to take action — especially action such as sending sensitive information, clicking on a link, or downloading an attachment — exercise caution and look for other telltale signs of phishing attacks. Don’t hesitate to contact the company directly; they can verify legitimacy and may not even be aware that their name is being used for fraud.
- Never, ever share your password. Did we say never? Yes, we mean never. Your password is the key to your identity, your data, and your classmates’ and colleagues’ data. It is for your eyes only. K-State will never ask you for your password in an email.
- Avoid opening links and attachments from unknown senders. Get into the habit of typing known URLs into your browser. Don’t open attachments unless you’re expecting a file from someone. Give them a call if you’re suspicious.
- When you’re not sure, call to verify. Let’s say you receive an e-mail claiming to be from someone you know — a friend, colleague, or even the K-State president. Cybercriminals often spoof addresses to convince you, then request that you perform an action such as transfer funds or provide sensitive information. If something seems off about the e-mail, call them at a known number listed in the K-State search directory to confirm the request.
A few more tips about phishing:
- Phishing isn’t confined to just e-mail! Cybercriminals will also launch phishing attacks through phone calls, text messages, or other online messaging applications. Don’t know the sender or caller? Seem too good to be true? It’s probably a phishing attack.
- Don’t talk to strangers! Receive a call from someone you don’t know? Are they asking you to provide information or making odd requests? Hang up the phone and report it to abuse@k-state.edu.
- Don’t be tempted by abandoned flash drives. Cybercriminals may leave flash drives lying around for victims to pick up and insert, thereby unknowingly installing malware on their computers. You might be tempted to insert a flash drive only to find out the rightful owner, but be wary — it could be a trap.
Source: Adapted from Educause Campus Security Awareness Campaign
If you have any questions about phishing scams, contact the IT Help Desk, helpdesk@k-state.edu, 532-7722.